Authentication (uses symmetric key system)
If A wants to prove its identity to B, that's authentication. Or more precisely, it's an End-point authentication. If A was able to visit B, then it would be super easy to prove its identity. But in the network, the only way that authentication can be done is via packets sent over the network.
Authentication of A to B:
A sends 'hello' to B. A receives nonce 'r' (number used once in a lifetime) from B. A sends K(r) to B.
Preconditions: K is a symmetric key that A and B has between them before this exchange.
Guarantees: no playback attack (because nonce is valid for one-time use, then expires)
Email security (uses both public key system and symmetric key system)
A to send email to B:
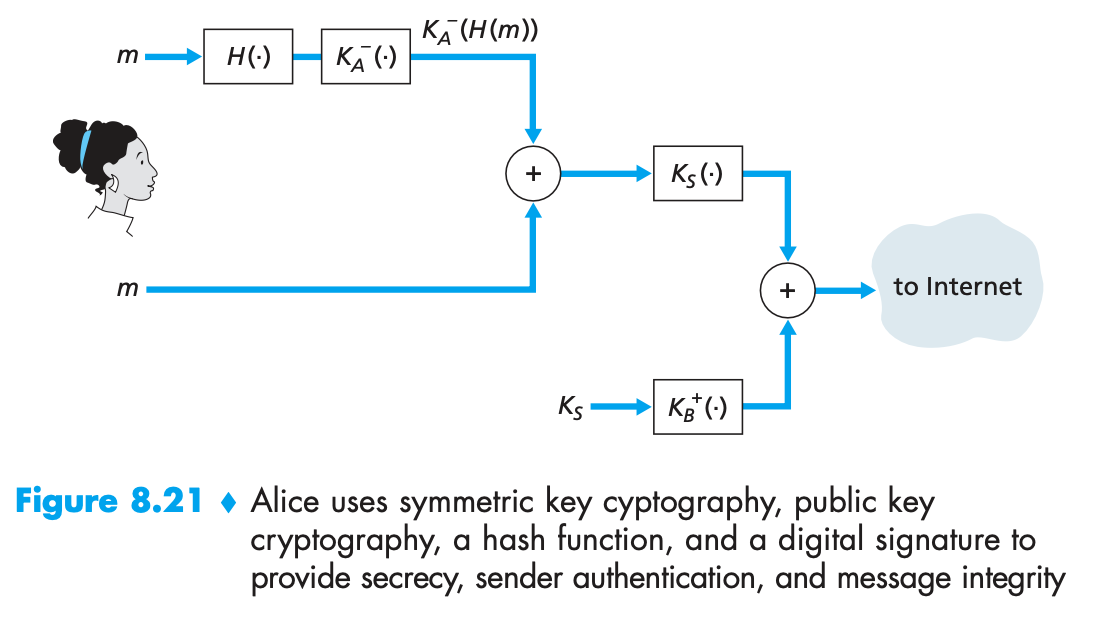
This method guarantees guarantee:
- Receiver authentication: Ks can only be retrieved by B.
- Sender authentication: A's digital signature, privKeyOfA(H(m)), can be verified by B using pubKeyOfA
- Message integrity: tampering of m can be detected by B through H(m) matching
- Confidentiality: Ks is used for symmetric key system that encrypts message m.
SSL (uses both public key system and symmetric key system)
SSL is a protocol that sits at the bottom of application layer, and is 's' of 'https'.
It works in these steps:
1. TCP handshake
2. SSL handshake
3. Key derivation
4. Data transfer
SSL handshake is a little bit complex
- Client sends [nonce] to Server.
- Server sends [nonce, certificate, algorithm for encryption], where the algorithm chooses:
symmetric algorithm (eg AES)
public key algorithm (eg RSA)
MAC algorithm
- Client learns K+{server}, and creates PMS, and sends K+{server}(PMS) to server.
- Both client and server creates MS from nonces and PMS
- Client sends MAC(all sent messages) to Server, which Server checks against MAC(all received messages), vice versa. This prevents that the messages so far weren't tampered. The fact that nonce is part of these checks means that playback attack is prevented too.
Key derivation is a little bit funky
I don't fully understand what's happening, but we are using the shared MS to create 2 MAC keys and 2 encryption keys, all of which will be available for both client and server.
Data transfer
Simplest way to understand it is that we are using MS (symmetric key) for encryption. I'm not exactly sure how the decomposed version of MS (2 MAC keys and 2 encryption keys) is allowing for symmetric key system communication, so it's easier if you think of it as single MS key being used for encrypted communication.